Introduction to Blockchain and the Trust Triangle
Blockchain technology is revolutionizing the way we manage our digital identities, shifting from traditional centralized databases—prone to massive data breaches—to a decentralized and secure system. This advanced technology functions as a digital ledger, duplicated across numerous computers worldwide, making any attempt to alter information virtually impossible due to the sheer number of copies that would need to be changed simultaneously. This characteristic of immutability is what makes blockchain an ideal solution for securing digital identities. With blockchain, sensitive credentials like diplomas, passports, or medical records can be securely stored and controlled directly by users, who can selectively share information with specific entities. This transition to a decentralized model not only enhances security but also promotes transparency and places control back in the hands of users, heralding a new era of trust and efficiency in digital identity management.
The Trust Triangle and How it Works
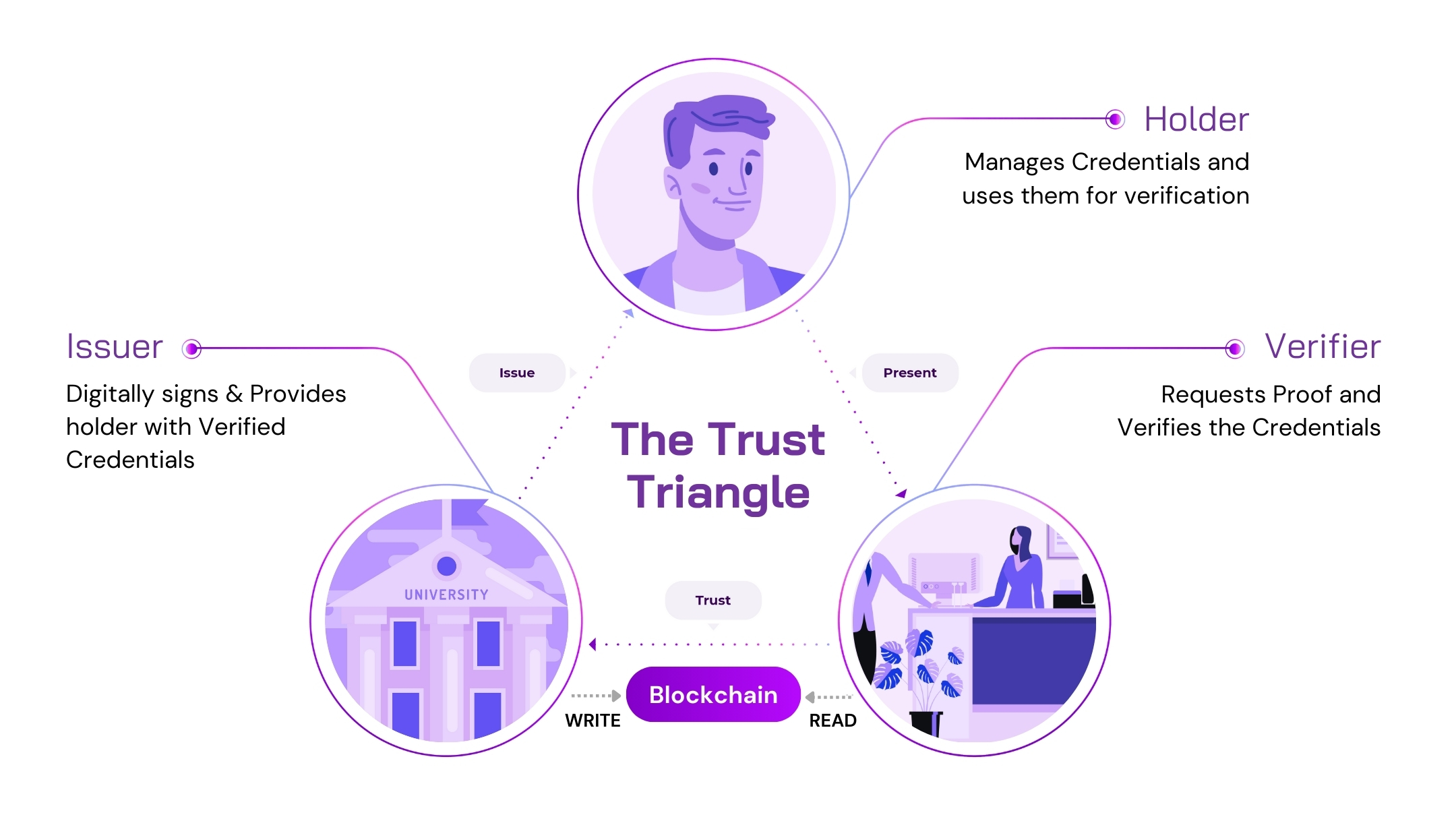
In today's digital world, managing our online identities can be a challenge. Traditional systems often rely on centralized authorities to store and control our data. However Decentralized Identity (DID) offers a new approach, putting individuals in control of their information. This system revolves around the Trust Triangle, which consists of three key players: issuers, holders, and verifiers.
1. Issuers are entities authorized to create and distribute trusted digital records. These can be institutions like governments and universities, or even personal connections such as friends or family.
2. Holders are individuals who possess these digital records, known as Verifiable Credentials. These credentials serve as secure, tamper-proof documents detailing personal attributes or qualifications. Holders manage these credentials within digital wallet apps, maintaining control over their data.
3. Verifiers are organizations or entities that require validation of the information a holder presents, such as a bank needing identity confirmation for account setup, or a website verifying age.
Building Trust: The issuer first establishes their identity on a blockchain, a secure digital ledger. This acts like a public registry for the issuer's digital signature, allowing verifiers to confirm its authenticity later.
Issuing Credentials: Once their identity is established, the issuer can create Verifiable Credentials for holders. This happens through a secure, private connection between the issuer and the holder. The credential contains the issuer's digital signature, linking it back to the trusted record on the blockchain.
Taking Control: The holder receives the credential in their digital wallet. This gives them complete control over their data. They can choose what information to share and with whom.
Verifying Information: A verifier who could be an employer, for example, can send a verification request to a holder’s wallet. The holder then presents a Verifiable credential to the verifier which includes only the relevant information for that request. The verifier can then use the blockchain to check the authenticity of the issuer's signature and the validity of the holder’s credential.
This decentralized approach empowers individuals with control over their data and fosters trust in online interactions.
Enhancing Digital Identity with Verifiable Credentials (VCs)
Trust is the most important thing in today's digital world. When we carry out various transactions online, it's often difficult to verify the legitimacy of the person we're interacting with. This is true for everything from secure financial transactions to hiring the right talents. Verifiable Credentials (VCs) are starting to be used in the blockchain space to fix this problem and make the internet more trustworthy.
What are Verifiable Credentials?
Think of VCs as secure, digital badges issued by reliable sources such as universities or government bodies. These credentials contain verifiable claims about a subject, which could be an individual, a group, or even a machine. For example, a VC might verify that a person has graduated from a particular university, holds a professional license, or meets age requirements for certain activities.
Why are VCs Important?
There are a few reasons why VCs are better than the ways we check credentials right now. Unlike pieces of paper that say you finished school (diplomas), VCs are very hard to forge because they are kept safe by cryptography. When a VC is created, it is signed on a shared ledger that can't be changed. This shows where the VC came from and that it is real.
How do VCs Create Trust?
VCs let people have more control over who they are online. When you need to prove something to someone (like that you are old enough to buy something), you can choose which claims to show them instead of giving them the whole badge. This protects your privacy while still letting them check. For example, if you wanted to buy something online that asked if you were 18 or older, you could use a VC to show the store that you are old enough without telling them your birthday.
VCs also make it easier to check if something is true or not. The person who needs to verify a VC can do it right away. They don't need to call anyone at the school who gave you the diploma to make sure you didn't fake it. This creates a more trustless digital experience for everyone.
Use Case: Enhancing Airport Security with Verifiable Credentials and Zero-Knowledge Proofs (ZKPs)
Consider Alice, a frequent traveler who utilizes Verifiable Credentials (VCs) alongside Zero-Knowledge Proofs (ZKPs) to optimize her airport security process. Before traveling, Alice secures digital versions of her passport, visa, and health certification, stored in a secure digital wallet on her smartphone.
At the Airport:
1. Check-in: Alice presents her digital passport and visa from her wallet. Using ZKP, the airline verifies these documents without needing to see the actual data, ensuring Alice's personal information remains private.
2.Security and Border Control: For security checks, Alice uses ZKP to prove her identity and travel authorization without exposing any personal details. The system confirms she meets all criteria without actually viewing the data.
3. Boarding: At the gate, Alice once again uses her digital passport, verified via ZKP, ensuring a secure and private boarding process.
Benefits:
Efficiency: Streamlines verification processes, significantly reducing wait times.
Security: Enhances security as ZKPs prevent actual data exposure, minimizing forgery risks.
Privacy: ZKPs allow Alice to prove her credentials without revealing underlying personal information, maintaining privacy.
Existing Real-World Applications of Blockchain-Based Digital Identities:
Buenos Aires, Argentina: The government of Buenos Aires has launched a new decentralized digital identity protocol using an application built on Matter Labs’ zkSync Era rollup. This program, known as QuarkID, allows citizens to download a wallet app and claim key personal identification documents such as birth and marriage certificates. This initiative enables Buenos Aires residents to own and manage their personal data directly
Turkey has implemented a blockchain-based digital identity system for its online public services portal, E-Devlet. This system allows Turkish citizens to use a blockchain-based digital identity to log into the portal and access various services. The integration of blockchain technology is aimed at enhancing the security and accessibility of government services online
Estonia's e-Residency Program: Estonia offers a digital identity to non-Estonians, allowing them to operate businesses within the EU. This program utilizes blockchain technology to secure digital identities, enabling e-residents to sign documents, access secure services, and conduct banking activities online.
Zug, Switzerland's Blockchain-Based ID System: The city of Zug in Switzerland has implemented a blockchain-based digital identity service for its residents. This service allows citizens to participate in online voting and proves the security and efficiency of blockchain in managing citizen identities.
Alastria ID Model in Spain: Alastria, a consortium of over 500 companies, has developed a national blockchain ecosystem in Spain, including a standardized digital identity model. This model allows users to have a single, verified digital identity usable across various services within the network.
The adoption and scalability of digital identity solutions using blockchain technology are pivotal for the growth and practical implementation of Web3. As these systems become more integrated into daily activities—ranging from health care and finance to education and government services—they not only solve real-world problems of identity verification and fraud prevention but also pave the way for a more interconnected and decentralized internet.
The use of decentralized identifiers (DIDs) and verifiable credentials underscores a shift towards user-controlled data, which is at the heart of Web3's ethos. This transformation not only enhances security and privacy but also promotes a seamless user experience across global services. As digital identities become more widespread, they could accelerate the adoption of Web3 by providing a reliable and scalable framework that supports a wide range of applications in a trustless environment, thereby driving innovation and inclusivity in the digital space.
The Future of Digital Identity: Paving the Way for Web3